Remote work is amazing until it isn’t.
You’ve got people designing in Figma from a beach, closing deals over Zoom in coffee shops, or spinning up code while waiting at the airport. It’s fast, flexible, and kind of magical. But here’s the catch: behind every click, every shared file, every remote login, there’s one thing quietly holding it all together — credentials.
And if the wrong person gets hold of those credentials, things can go downhill fast.

That is why credential management is extremely significant, now more than ever. Not just about recording passwords in a safe vault, but about power over who gains access to what and when. From protecting company credentials to rotating security credentials and setting up MFA, it’s how you make sure your digital front door stays locked, and only the right people have the keys.
Luckily, tools like DeskIn make remote access security a whole lot easier (and smarter). In this blog, we’ll break down what credential management is, how it works, and how you can use it to lock down your setup without locking out your team.
Let’s get into it.
What Is Credential Management?
Every password, API token, SSH key, certificate, or fingerprint scan is basically a key to something important in your company’s digital world. And let’s be honest, keeping track of a few keys is easy, but hundreds or thousands, that’s a recipe for lost logins, accidental oversharing, or worse, a security breach.
This is where credential management comes into play. The system that is holding all those keys keeps them safely locked away until they are only given to the right person at the correct time.
A better way to consider credential management is not as a dusty password list but as a virtual bouncer that knows who should and shouldn't have access, makes sure the right people are let in, and the wrong people are kept out.
Properly implemented credential management allows your team to operate unblocked while preventing hackers and other unwanted guests from getting inside.
Four Jobs Every Strong Credential Management System Handles
A proper credential management setup works like a full-time security team for your logins. Here’s what it does:
Store securely – Encrypts credentials and keeps them in a secure vault, far away from sticky notes or unprotected files.
Retrieve safely – Delivers credentials only to authorized users, without showing them in plain text or risking a copy-paste leak.
Update automatically – Rotate passwords, refresh tokens, and update certificates to prevent expiration/exploitation.
Revoke instantly – Cuts off access the moment someone leaves the team or changes roles, leaving no back doors open.
Why Credential Management Is the Backbone of Security
Credential management is the foundation of secure authentication and identity management; without it, every other security measure becomes weaker.
Secure authentication – Confirms each user's identity, adds layers of protection like MFA, and stops risky habits like credential reuse.
Identity management – Connects every credential to a specific role or permission so users only get access to what they truly need, while keeping a clear, auditable trail of every action.
In short, credential management doesn’t just protect passwords; it helps safeguard the core digital operations of your business.
Understanding Credential Types & Their Security Functions

There are different levels of credentials for a reason. They each serve a different purpose, and it is important to understand how to work with them in order to keep remote work secure. A strong credential management system doesn't just store these credentials; it knows what combination to use, when, and where. So, here are the main types and why they matter.
Passwords
The classic credential, simple, familiar, and unfortunately, still a favorite target for attackers. Weak or reused passwords are an open invitation for trouble.
Used for: Email accounts, internal tools, VPNs, web apps.
SSH Keys
These cryptographic keys let you log into servers or developer environments without a password. They’re much harder to crack, but only if stored properly.
Used for: Remote server access, infrastructure management, cloud platforms.
API Tokens
Think of these as digital ID cards for software. They give systems permission to talk to each other securely, no human intervention required.
Used for: Integrations, automation, CI/CD pipelines, webhooks.
Biometrics
Your fingerprint, your face, your voice as the password. Fast, convenient, and tough to fake.
Used for: Mobile device logins, secure work apps, SSO tools.
Multi-Factor Authentication (MFA)
One lock is good, two or more are better. MFA adds extra layers of verification, like pairing a password with an app-generated code, biometric scan, or hardware key. Even if one factor is stolen, the attacker still can’t get in without the others.
Used for: Secure logins to remote work tools, SaaS apps, admin dashboards.
Certificates
Digital files that prove identity and encrypt communication between users, devices, and websites.
Used for: HTTPS, VPNs, S/MIME email, software signing.
Common Threats to Remote Credential Security
Remote work has transformed your team logins into digital keys that grant access to your most valuable data systems and customer trust. Without strong credential management, those keys can slip into the wrong hands faster than you think.
Here are some of the biggest threats going after secure credentials in remote work environments:
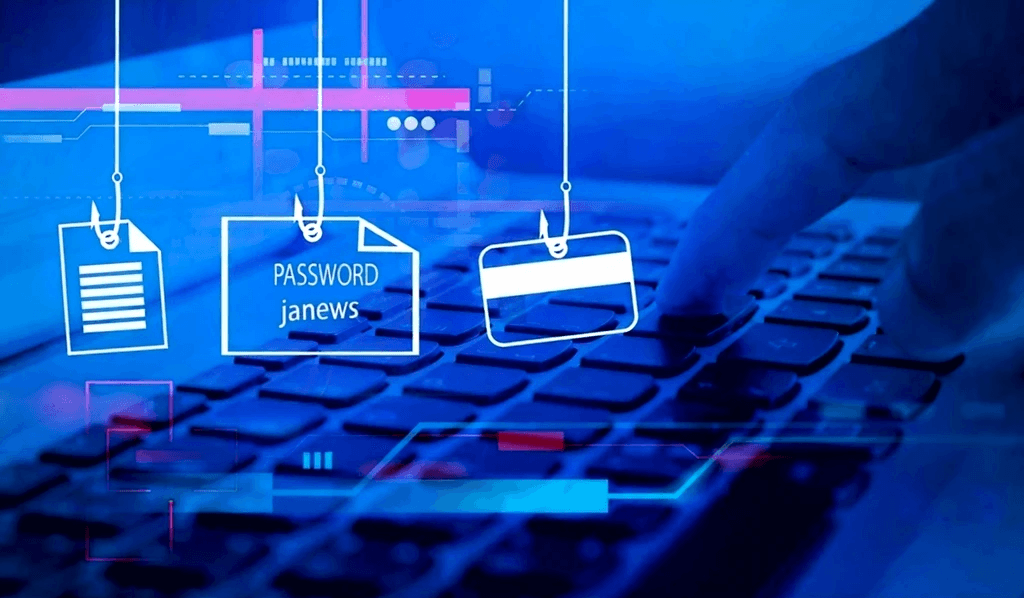
Phishing: Scammers use deceptive emails and chats and fake login pages to trick users into revealing their account information.
Keylogging: Malware secretly records everything typed, including usernames, passwords, and session tokens.
Brute-Force Attacks: Hackers use bots to rapidly guess username-password combos, targeting accounts that use weak or reused passwords.
Session Hijacking: Attackers intercept an active login session, also this action takes over access without needing the original credentials.
Many session-related breaches stem from misconfigured or outdated RDP settings. Learn more about RDP security risks and protections to keep your remote environments safe.
The Real-World Consequences
When credentials are compromised, it’s not just an inconvenience; it’s a business risk. Your organization would encounter:
Data theft: Confidential files, financial records, or customer information exposed.
Remote access abuse: Attackers moving freely through systems while posing as legitimate employees.
Downtime and disruption: IT teams racing to contain the breach while work grinds to a halt.
Compliance violations: Costly fines, penalties, and lasting damage to your reputation.
In short, one stolen login can lead to a chain reaction of security failures. That’s why proactive credential management, not reactive cleanup, is the smarter strategy.
Best Practices for Managing Credentials in Remote Work
Here are key remote access security best practices to keep your team’s credential access safe, streamlined, and secure:
Use Encrypted Storage: Store all security credentials — passwords, SSH keys, API tokens — in encrypted vaults like Bitwarden or 1Password. For high-risk systems, use hardware-based options like YubiKeys or HSMs to prevent unauthorized access.
Enforce Two-Factor or Multi-Factor Authentication (2FA/MFA): Always require at least two forms of verification (e.g., password + app code). MFA blocks most unauthorized access attempts, even when passwords are compromised.
Rotate Passwords & Audit Access Regularly: Set password expiration policies and rotate credentials regularly. Review who has access and remove inactive users to minimize risks and meet compliance requirements.
Stop Sharing Credentials Across Team Members: Shared logins create security gaps and accountability issues. Instead, assign individual accounts with role-based access. Use SSO or identity providers to manage permissions easily.
Set Session Timeouts and Auto-Logoff: Auto-logoff inactive sessions to prevent misuse of unattended devices. Especially in remote work environments, this is a simple but powerful layer of protection.
Want to go deeper on securing your remote desktop itself? Here’s a full guide on how to set up a secure remote desktop setup the right way.
Key Benefits of Strong Credential Management
A strong credential management system doesn’t just protect your business; it improves how your teams work, how you meet compliance, and how you scale securely in a remote work environment.
Here’s what your organization stands to gain:
1. Enhanced Security
Strong credential management helps prevent weak password reuse, phishing attacks, and unauthorized access. With features like MFA and encrypted vaults, your security credentials stay protected even across remote networks and devices.
2. Streamlined Operations
Centralized company credentials control cuts admin work. Automated rotation and clear role-based permissions make onboarding and offboarding quick and secure.
3. Regulatory Compliance
From GDPR to HIPAA, proper credential access controls help meet global compliance standards. Audit logs, encryption, and least privilege enforcement ensure you’re prepared for any security review or data protection audit, without extra overhead.
4. Reduced Insider Threats
Granular access controls limit over-permissioned users, while session monitoring helps flag suspicious activity. Temporary credentials and timeout features reduce the long-term risk of credential misuse, intentional or not.
5. Improved Remote Productivity
Tools like single sign-on (SSO) and secure vaults eliminate login friction. Users authenticate once and access what they need, no password juggling or downtime. It’s secure, smooth, and perfect for a growing remote work team.
How DeskIn Helps Secure Remote Sessions
DeskIn is a fast, secure remote access platform designed for modern teams. From IT to creative work, it helps users connect and collaborate safely from anywhere.
Even the strongest passwords can’t protect your business if your remote access platform isn’t built for security. That’s where DeskIn steps up, combining performance with enterprise-grade credential management to keep every remote session locked down and in your control.

Secure Login Flows
DeskIn doesn’t just let anyone in. It uses secure login methods like device code pairing and session approval, ensuring only verified users can access a remote device. Whether you’re working from home or halfway around the world, DeskIn enforces strong identity verification before any session begins.
Session Encryption
Every session on DeskIn is protected with full encryption, ensuring that your data remains secure during transmission. This end-to-end protection keeps sensitive information safe from interception, even over public or unsecured networks.
Credential Protection for Unattended Access
Need to access a remote system while you’re away from your desk? DeskIn supports unattended access, but with safeguards in place. Your secure credentials are still protected by layered authentication, and access can be logged and monitored for full visibility.
Trusted Device Management
With DeskIn, you’re in full control of who gets in and from where. Using device whitelisting, you can ensure that only pre-approved devices connect to your systems. Whether it’s a single laptop or an entire fleet of team smartphones, you get centralized control without losing the flexibility remote work demands.
DeskIn isn’t just another remote access tool; it’s a security-first platform built with strong credential management, remote access security, and real-time oversight at its core. From remote design teams to IT support to distributed dev squads, DeskIn keeps every session locked down, every connection accountable, and every workflow running smoothly.
If you’re looking to lock down your system end-to-end, don’t miss this guide on how to secure your remote desktop.
Credential Management with DeskIn: Simple, Secure, and Remote-Ready
Remote security starts with strong credential management, not after the login, but before it even begins. Managing credentials properly is the foundation of safe, seamless remote access security.
DeskIn supports this at every level, from secure login flows to encrypted sessions and device-level access control. It helps your team stay productive while keeping company credentials and systems protected.
Now’s the time to review your setup. Audit your credential policies, eliminate weak spots, and use tools like DeskIn to lock down remote sessions, the right way.
Ready to take control of your remote access security? Download DeskIn now and secure every login.
Still comparing your options? Check out our breakdown of the 10 best secure remote desktop software, and see why DeskIn leads the pack for both security and performance.

Remote work is amazing until it isn’t.
You’ve got people designing in Figma from a beach, closing deals over Zoom in coffee shops, or spinning up code while waiting at the airport. It’s fast, flexible, and kind of magical. But here’s the catch: behind every click, every shared file, every remote login, there’s one thing quietly holding it all together — credentials.
And if the wrong person gets hold of those credentials, things can go downhill fast.

That is why credential management is extremely significant, now more than ever. Not just about recording passwords in a safe vault, but about power over who gains access to what and when. From protecting company credentials to rotating security credentials and setting up MFA, it’s how you make sure your digital front door stays locked, and only the right people have the keys.
Luckily, tools like DeskIn make remote access security a whole lot easier (and smarter). In this blog, we’ll break down what credential management is, how it works, and how you can use it to lock down your setup without locking out your team.
Let’s get into it.
What Is Credential Management?
Every password, API token, SSH key, certificate, or fingerprint scan is basically a key to something important in your company’s digital world. And let’s be honest, keeping track of a few keys is easy, but hundreds or thousands, that’s a recipe for lost logins, accidental oversharing, or worse, a security breach.
This is where credential management comes into play. The system that is holding all those keys keeps them safely locked away until they are only given to the right person at the correct time.
A better way to consider credential management is not as a dusty password list but as a virtual bouncer that knows who should and shouldn't have access, makes sure the right people are let in, and the wrong people are kept out.
Properly implemented credential management allows your team to operate unblocked while preventing hackers and other unwanted guests from getting inside.
Four Jobs Every Strong Credential Management System Handles
A proper credential management setup works like a full-time security team for your logins. Here’s what it does:
Store securely – Encrypts credentials and keeps them in a secure vault, far away from sticky notes or unprotected files.
Retrieve safely – Delivers credentials only to authorized users, without showing them in plain text or risking a copy-paste leak.
Update automatically – Rotate passwords, refresh tokens, and update certificates to prevent expiration/exploitation.
Revoke instantly – Cuts off access the moment someone leaves the team or changes roles, leaving no back doors open.
Why Credential Management Is the Backbone of Security
Credential management is the foundation of secure authentication and identity management; without it, every other security measure becomes weaker.
Secure authentication – Confirms each user's identity, adds layers of protection like MFA, and stops risky habits like credential reuse.
Identity management – Connects every credential to a specific role or permission so users only get access to what they truly need, while keeping a clear, auditable trail of every action.
In short, credential management doesn’t just protect passwords; it helps safeguard the core digital operations of your business.
Understanding Credential Types & Their Security Functions

There are different levels of credentials for a reason. They each serve a different purpose, and it is important to understand how to work with them in order to keep remote work secure. A strong credential management system doesn't just store these credentials; it knows what combination to use, when, and where. So, here are the main types and why they matter.
Passwords
The classic credential, simple, familiar, and unfortunately, still a favorite target for attackers. Weak or reused passwords are an open invitation for trouble.
Used for: Email accounts, internal tools, VPNs, web apps.
SSH Keys
These cryptographic keys let you log into servers or developer environments without a password. They’re much harder to crack, but only if stored properly.
Used for: Remote server access, infrastructure management, cloud platforms.
API Tokens
Think of these as digital ID cards for software. They give systems permission to talk to each other securely, no human intervention required.
Used for: Integrations, automation, CI/CD pipelines, webhooks.
Biometrics
Your fingerprint, your face, your voice as the password. Fast, convenient, and tough to fake.
Used for: Mobile device logins, secure work apps, SSO tools.
Multi-Factor Authentication (MFA)
One lock is good, two or more are better. MFA adds extra layers of verification, like pairing a password with an app-generated code, biometric scan, or hardware key. Even if one factor is stolen, the attacker still can’t get in without the others.
Used for: Secure logins to remote work tools, SaaS apps, admin dashboards.
Certificates
Digital files that prove identity and encrypt communication between users, devices, and websites.
Used for: HTTPS, VPNs, S/MIME email, software signing.
Common Threats to Remote Credential Security
Remote work has transformed your team logins into digital keys that grant access to your most valuable data systems and customer trust. Without strong credential management, those keys can slip into the wrong hands faster than you think.
Here are some of the biggest threats going after secure credentials in remote work environments:
Phishing: Scammers use deceptive emails and chats and fake login pages to trick users into revealing their account information.
Keylogging: Malware secretly records everything typed, including usernames, passwords, and session tokens.
Brute-Force Attacks: Hackers use bots to rapidly guess username-password combos, targeting accounts that use weak or reused passwords.
Session Hijacking: Attackers intercept an active login session, also this action takes over access without needing the original credentials.
Many session-related breaches stem from misconfigured or outdated RDP settings. Learn more about RDP security risks and protections to keep your remote environments safe.

The Real-World Consequences
When credentials are compromised, it’s not just an inconvenience; it’s a business risk. Your organization would encounter:
Data theft: Confidential files, financial records, or customer information exposed.
Remote access abuse: Attackers moving freely through systems while posing as legitimate employees.
Downtime and disruption: IT teams racing to contain the breach while work grinds to a halt.
Compliance violations: Costly fines, penalties, and lasting damage to your reputation.
In short, one stolen login can lead to a chain reaction of security failures. That’s why proactive credential management, not reactive cleanup, is the smarter strategy.
Best Practices for Managing Credentials in Remote Work
Here are key remote access security best practices to keep your team’s credential access safe, streamlined, and secure:
Use Encrypted Storage: Store all security credentials — passwords, SSH keys, API tokens — in encrypted vaults like Bitwarden or 1Password. For high-risk systems, use hardware-based options like YubiKeys or HSMs to prevent unauthorized access.
Enforce Two-Factor or Multi-Factor Authentication (2FA/MFA): Always require at least two forms of verification (e.g., password + app code). MFA blocks most unauthorized access attempts, even when passwords are compromised.
Rotate Passwords & Audit Access Regularly: Set password expiration policies and rotate credentials regularly. Review who has access and remove inactive users to minimize risks and meet compliance requirements.
Stop Sharing Credentials Across Team Members: Shared logins create security gaps and accountability issues. Instead, assign individual accounts with role-based access. Use SSO or identity providers to manage permissions easily.
Set Session Timeouts and Auto-Logoff: Auto-logoff inactive sessions to prevent misuse of unattended devices. Especially in remote work environments, this is a simple but powerful layer of protection.
Want to go deeper on securing your remote desktop itself? Here’s a full guide on how to set up a secure remote desktop setup the right way.
Key Benefits of Strong Credential Management
A strong credential management system doesn’t just protect your business; it improves how your teams work, how you meet compliance, and how you scale securely in a remote work environment.
Here’s what your organization stands to gain:
1. Enhanced Security
Strong credential management helps prevent weak password reuse, phishing attacks, and unauthorized access. With features like MFA and encrypted vaults, your security credentials stay protected even across remote networks and devices.
2. Streamlined Operations
Centralized company credentials control cuts admin work. Automated rotation and clear role-based permissions make onboarding and offboarding quick and secure.
3. Regulatory Compliance
From GDPR to HIPAA, proper credential access controls help meet global compliance standards. Audit logs, encryption, and least privilege enforcement ensure you’re prepared for any security review or data protection audit, without extra overhead.
4. Reduced Insider Threats
Granular access controls limit over-permissioned users, while session monitoring helps flag suspicious activity. Temporary credentials and timeout features reduce the long-term risk of credential misuse, intentional or not.
5. Improved Remote Productivity
Tools like single sign-on (SSO) and secure vaults eliminate login friction. Users authenticate once and access what they need, no password juggling or downtime. It’s secure, smooth, and perfect for a growing remote work team.
How DeskIn Helps Secure Remote Sessions
DeskIn is a fast, secure remote access platform designed for modern teams. From IT to creative work, it helps users connect and collaborate safely from anywhere.
Even the strongest passwords can’t protect your business if your remote access platform isn’t built for security. That’s where DeskIn steps up, combining performance with enterprise-grade credential management to keep every remote session locked down and in your control.

Secure Login Flows
DeskIn doesn’t just let anyone in. It uses secure login methods like device code pairing and session approval, ensuring only verified users can access a remote device. Whether you’re working from home or halfway around the world, DeskIn enforces strong identity verification before any session begins.
Session Encryption
Every session on DeskIn is protected with full encryption, ensuring that your data remains secure during transmission. This end-to-end protection keeps sensitive information safe from interception, even over public or unsecured networks.
Credential Protection for Unattended Access
Need to access a remote system while you’re away from your desk? DeskIn supports unattended access, but with safeguards in place. Your secure credentials are still protected by layered authentication, and access can be logged and monitored for full visibility.
Trusted Device Management
With DeskIn, you’re in full control of who gets in and from where. Using device whitelisting, you can ensure that only pre-approved devices connect to your systems. Whether it’s a single laptop or an entire fleet of team smartphones, you get centralized control without losing the flexibility remote work demands.
DeskIn isn’t just another remote access tool; it’s a security-first platform built with strong credential management, remote access security, and real-time oversight at its core. From remote design teams to IT support to distributed dev squads, DeskIn keeps every session locked down, every connection accountable, and every workflow running smoothly.
If you’re looking to lock down your system end-to-end, don’t miss this guide on how to secure your remote desktop.
Credential Management with DeskIn: Simple, Secure, and Remote-Ready
Remote security starts with strong credential management, not after the login, but before it even begins. Managing credentials properly is the foundation of safe, seamless remote access security.
DeskIn supports this at every level, from secure login flows to encrypted sessions and device-level access control. It helps your team stay productive while keeping company credentials and systems protected.
Now’s the time to review your setup. Audit your credential policies, eliminate weak spots, and use tools like DeskIn to lock down remote sessions, the right way.
Ready to take control of your remote access security? Download DeskIn now and secure every login.
Still comparing your options? Check out our breakdown of the 10 best secure remote desktop software, and see why DeskIn leads the pack for both security and performance.